- Vrealmatic
- Mikrotik Router
- Firewall
- Filter Rules
Filter Rules Firewall configuration on Mikrotik Router
No matter which MikroTik router you have, its operating system and the administrative interface, RouterOS, are always the same. This wiki page describes the function and settings of the Firewall.

The Essence of Filter Rules Function
Filter Rules serve to define firewall rules that determine how the router processes incoming and outgoing network traffic. Through Firewall rules, you can control access to network resources, block unwanted traffic, limit network attacks, and implement other security policies.
By default, MikroTik RouterOS operates on a "default deny" principle. The "default deny" or "implicitly reject" concept in firewall rules means that all network traffic not explicitly allowed through defined rules is automatically blocked.
Through firewall rules, you specify:
- access conditions from the outside to the router (
chain=input) only traffic related to router management - ssh, webfig, etc - access conditions from the outside to devices behind the router (
chain=forward) - access conditions from devices behind the router to the internet (
chain=output)
RouterOS in factory settings already has several predefined filter rules enabling commonly requested functionality, such as the ability for devices behind the router to access the internet. The significance of individual rules can be found in the predefined rules section.
Overview of Set Rules on the Router
- In terminal:
/ip/firewall/filter. Listing by commandprint. - In Webfig/Winbox:
Filter Rulestab inIP/Firewallsection.
Explanation of Predefined Rules
The screenshot below is from the Webfig environment (service www), section IP/Firewall → tab Filter Rules.
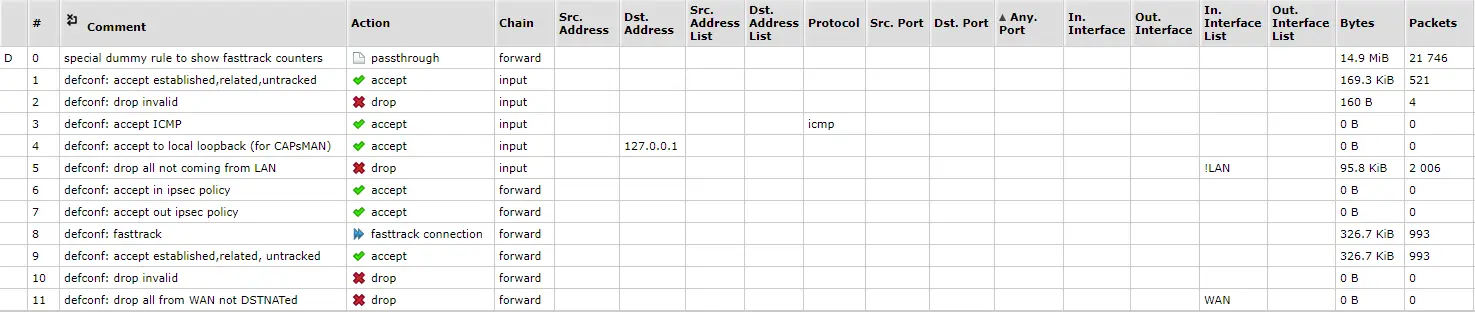
Below is a terminal record of each of the rules above with an explanation of its function.
0 D ;;; special dummy rule to show fasttrack counters chain=<mark>forward</mark> action=passthroughA special rule to display counters for FastTrack traffic. The rule itself does not apply any specific action to the traffic (it's a
passthroughaction) - its primary purpose is to allow monitoring and displaying statistics for FastTracked traffic within the firewall.1 ;;; defconf: accept established,related,untracked chain=input action=accept connection-state=established,related,untrackedAllows traffic that is marked as already established, related, or untracked - in other words, traffic that is already known to the router as part of an existing connection or is somehow related to it. This includes responses to requests sent from your local network, which is necessary for the normal operation of, for example, internet applications. This rule ensures that responses to requests sent from your network to the internet are accepted back through the firewall.
2 ;;; defconf: drop invalid chain=input action=drop connection-state=invalidDrop Invalid: Discards any traffic considered invalid or corrupted.
3 ;;; defconf: accept ICMP chain=input action=accept protocol=icmpAllows handling of ICMP (Internet Control Message Protocol) traffic. ICMP is a key protocol used on the internet for diagnostic purposes and network management, most famous for its role in
pingand traceroute operations, which allow testing the availability and path of network connections.4 ;;; defconf: accept to local loopback (for CAPsMAN) chain=input action=accept dst-address=127.0.0.1Allows inbound (
input) traffic directed to the local loopback interface, typically identified by IP address127.0.0.1. This rule is essential for a number of internal processes and services running on the router, and may be particularly important for functions such as the CAPsMAN (Centralized Access Point Management) system for centralized management of wireless access points.5 ;;; defconf: drop all not coming from LAN chain=input action=drop in-interface-list=!LANA standard security measure that enhances the security of your device by blocking all incoming traffic on the input interface that does not come from the local network (LAN).
6 ;;; defconf: accept in ipsec policy chain=<mark>forward</mark> action=accept ipsec-policy=in,ipsecAllows traffic that is part of a defined IPSec policy through the router. Key aspects of this rule are designed to ensure that the router accepts incoming encrypted and secure IPSec traffic that is intended for devices in your network or originating from your network and heading inwards.
The goal of the rule is to enable secure and encrypted traffic through IPSec tunnels or connections that were established to secure communication between two points (for example, between two branches of a company, or between an end-user and a VPN server). By allowing this traffic, the router facilitates:
- Secure communication between networks or devices protected by IPSec.
- Protection of sensitive data during transmission over insecure networks, such as the internet.
IPSec is widely used for creating VPNs (Virtual Private Networks), securing remote access, and protecting data in transit between different networks. Therefore, this rule plays a key role in simplifying security policy management by automatically allowing all traffic that is already considered secure due to the application of IPSec policies, while ensuring that unencrypted or unauthorized traffic remains blocked.
7 ;;; defconf: accept out ipsec policy chain=<mark>forward</mark> action=accept ipsec-policy=out,ipsecSimilarly to the previous rule, but while rule no. 6 allows incoming IPSec traffic, rule no. 7 specifically permits outgoing encrypted and secure IPSec traffic passing through the router. This rule is essential for the proper function of IPSec VPNs, as it ensures that all traffic defined in IPSec policies and heading out of your network is allowed to pass through the firewall without restrictions.
8 ;;; defconf: fasttrack chain=<mark>forward</mark> action=fasttrack-connection hw-offload=yes connection-state=established,relatedEnables "fasttrack" connections for traffic that has already been established and is related. FastTrack is an optimization that significantly increases the throughput of the router for regular traffic.
action=fasttrack-connectionis applied to traffic that matchesconnection-state=established,related, which are connections that have already been established (e.g., regular internet browsing) or are in some way connected to an existing connection. This rule effectively allows fast passage for most outgoing traffic from the local network.9 ;;; defconf: accept established,related, untracked chain=<mark>forward</mark> action=accept connection-state=established,related,untrackedAccept Established, Related, Untracked: Similar to input, but for traffic passing through the router to devices behind the router.
10 ;;; defconf: drop invalid chain=<mark>forward</mark> action=drop connection-state=invalidDrop Invalid: Discards invalid passing traffic.
11 ;;; defconf: drop all from WAN not DSTNATed chain=<mark>forward</mark> action=drop connection-state=new connection-nat-state=!dstnat in-interface-list=WANDrop All from WAN Not DSTNATed: Blocks all new incoming traffic from WAN that is not targeted by a NAT rule, helping to protect the network from unwanted or potentially harmful traffic.
Additional Rules
X ;;; Remote Winbox access chain=input action=accept protocol=tcp dst-port=8291 log=no log-prefix=""Remote Winbox Access: Allows access to WinBox (TCP port 8291) from any address (no
src-addressspecified).X ;;; Allow IKE for IPSec chain=input action=accept protocol=udp dst-port=500 log=no log-prefix=""Allow IKE for IPSec: Allows Internet Key Exchange (UDP port 500), which is used for establishing IPSec tunnels.
X ;;; Allow L2TP chain=input action=accept protocol=udp dst-port=1701 log=no log-prefix=""Allow L2TP: Allows L2TP VPN traffic (UDP port 1701).
X ;;; Allow ESP for IPSec chain=input action=accept protocol=ipsec-esp log=no log-prefix=""Allow ESP for IPSec: Allows Encapsulating Security Payload, a part of the IPSec protocol for encrypted data transfer.
X ;;; Allow IPSec NAT-T chain=input action=accept protocol=udp in-interface=ether1 dst-port=4500 log=no log-prefix=""Allow IPSec NAT-T: Allows IPSec Network Address Translation Traversal (UDP port 4500) for scenarios where IPSec clients/server devices are behind NAT.
X ;;; Allow WebFig access from LAN chain=input action=accept protocol=tcp src-address=192.168.88.0/24 dst-port=443Allow WebFig Access from LAN: Allows access to the router's web interface (WebFig) for HTTPS (port 443) only from the LAN network (192.168.88.0/24).
X ;;; Allow WebFig access from LAN chain=input action=accept protocol=tcp src-address=192.168.88.0/24 dst-port=80Allow WebFig Access from LAN: Allows access to the router's web interface (WebFig) for HTTP (port 80) only from the LAN network (192.168.88.0/24).
Filter Rules Parameters and Actions:
To list Filter Rules, you can access them as follows:
- In the terminal:
/ip/firewall/filter. List with the commandprint. - In Webfig/Winbox: the
Filter Rulestab in theIP/Firewallsection.
The screenshot below is from the Webfig environment.
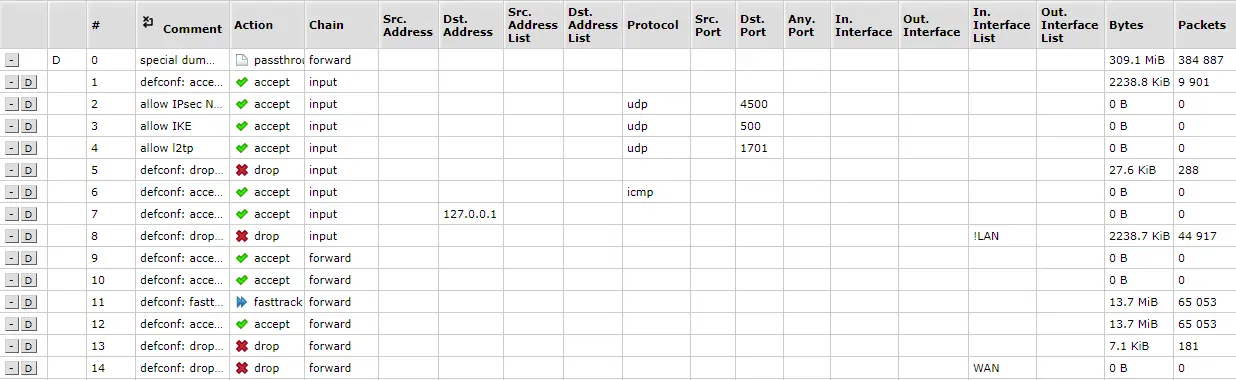
Column Descriptions / Parameter Purposes
- # (Number): Displays the sequential number of the rule within the firewall. This number is not fixed and can change if rules are added, removed, or moved.
- Comment: Provides space for a user comment on the rule, which may include a description of the rule or other notes for better orientation in the configuration.
- Action: Indicates the action to be taken if a packet matches the rule criteria.
- Chain: Identifies the chain to which the rule belongs.
input- incoming traffic to the router (router services and interfaces) - for example, login attempts via SSH or Winbox. Here, you can define rules to block unauthorized access or to allow traffic only from trusted sources.forward- traffic passing through the router, not intended for the router itself. This is traffic between different networks, for example, between the internal network and the internet. It is used to implement security policies for network traffic passing through the router, such as traffic filtering, restricting access to certain services or network segments, and protecting internal networks from potentially harmful traffic from the outside.output- outgoing traffic from the router - controls traffic generated by the router and heading out from it. It includes packets sent from the router to other devices or networks. It can be used for monitoring or limiting outgoing traffic from the router, such as system alerts, DNS queries, or firmware update attempts. This chain allows administrators to ensure that outgoing traffic from the router complies with security policies and is not exploited to spread malware or attacks.
- Src. Address: Displays the source IP address or range of addresses for which the rule applies. If this field is empty, the rule applies to all source traffic.
- Dst. Address: Displays the destination IP address or range of addresses for which the rule applies. If this field is empty, the rule applies to all destination traffic.
- Protocol: Specifies the network protocol to which the rule applies.
- Dst. Port: Specifies the destination port or range of ports for TCP or UDP protocols to which the rule applies.
- In. Interface: Identifies the incoming network interface through which the traffic must pass for the rule to apply.
- Out. Interface: Identifies the outgoing network interface used for rules in the
outputorforwardchain, specifying where the traffic is headed. - Bytes: Displays the total number of bytes that match the rule. This is useful for monitoring the amount of traffic affected by the rule.
- Packets: Shows the total number of packets that have passed through the rule. Similar to bytes, this is useful for monitoring the rule's activity.
Filter Actions
accept- Accept allows packets to pass through the firewall without further restrictions. If a rule with this action matches network traffic, the packet is accepted and continues its journey to the destination. Further rules for the packet are no longer evaluated.drop- Drop discards packets, meaning there will be no response. The attacker or source of packets will not have any explicit confirmation that the packet was dropped. Further rules for the packet are no longer evaluated.reject- Reject denies packets and, unlike drop, the firewall sends back a rejection message to the sender. Further rules for the packet are no longer evaluated.fasttrack- Fasttrack accelerates the passage of packets by removing them from the normal processing of the firewall. This feature is designed to improve the overall performance of the router by reducing the CPU load of the router when processing a large number of packets, especially for network traffic that does not need to go through all firewall checks, such as regular internet browsing or streaming traffic. Further firewall rules for this connection are mostly ignored.jump= jumps to another chain (rule set) within the firewall. It allows for organizing firewall rules into logical groups for better management and clarity. When a rule with the jump action matches a packet, processing moves to the specified chain.log= logs information about the packet to the system log. You can specify which information about the packet to log.passthrough- The passthrough action does not end the evaluation of rules for the packet. After applying a rule with this action, the packet will continue to go through other rules in the chain, thus allowing multiple actions for one packet, such as logging followed by redirection or filtering.return- Breaks processing in the current chain and returns to the parent chain if processing was started by a jump action.tarpit- Slows down communication with the attacker by keeping the TCP connection open but responding very slowly to any communication attempts.add dst to address list- Adds the destination (dst) IP address of the packet to a specified address list. This action does not affect further processing of the packet.add src to address list- Adds the source (src) IP address of the packet to a specified address list. Like the previous action, it does not affect further processing of the packet.
The Importance of Rule Ordering
Firewall rules are processed sequentially from top to bottom. When a network packet matches the criteria defined in a rule, that rule is applied. Depending on the specific action, the logical flow to subsequent rules may or may not continue. Therefore, proper organization of rules can enhance the router's performance by quickly processing the most common or critical traffic.
Tips for Choosing the Order of Rules
- FastTrack rule (chain=forward action=fasttrack-connection) enables faster processing of regular traffic by bypassing some further checks. It should be placed relatively high in the list of rules but after rules that reject invalid and potentially harmful traffic.
- Rules allowing access to commonly used services such as SSH, WinBox, WebFig, IKE for IPSec, and L2TP should be placed higher if you expect a high frequency of legitimate traffic for these services. However, it's also important to consider security risks and potentially place some restricting rules before them if you want to enhance security.
- Rules that restrict access from certain networks (e.g., chain=input action=accept src-address=192.168.88.0/24 for WebFig) are useful for increasing security, but at the same time, it's necessary to ensure they do not block legitimate traffic.
- Rejecting invalid traffic: (chain=input action=drop connection-state=invalid and chain=forward action=drop connection-state=invalid) is critical for enhancing the security of your network. These rules should be placed at the beginning of the relevant chains (input and forward) to eliminate invalid or corrupted packets as early as possible, which enhances overall security and helps save the router's processing time by preventing unnecessary processing of invalid packets.
- Rejecting unauthorized traffic:, which does not match any of the previous permissions (chain=input action=drop at the end of the input chain and chain=forward action=drop at the end of the forward chain), should be placed at the end of these chains. This ensures that all allowed traffic passes according to the specific rules set higher in the list, while all other traffic not explicitly permitted is rejected at the end of the process.
Changing the Order of Rules
- Winbox / Webfig: by dragging with the mouse (currently not working in Webfig)
- Terminal:
- List rules with the command
print. - Move a rule with the command
move numbers="[old rule no]" destination="[new rule no]"
- List rules with the command
Setting Up Firewall for Remote Access
By default, RouterOS does not allow access to the router through WAN. This can be enabled by adding the following rule.
- Go to the
Filter Rulestab in theIP/Firewallmenu (http://192.168.88.1/webfig/#IP:Firewall.Filter_Rules). - Use the
Add New/ or+button to navigate to the new rule creation menu. - Configure the rule parameters:
- Chain: Set to
input(this rule will apply to incoming traffic). - Protocol: Choose the protocol used for remote access (e.g.,
TCPfor RDP orSSH). - Dst. Port: Enter the port used for remote access (e.g.,
8291for Winbox,3389for RDP,22for SSH), see router services section. - Action: Set to
accept, which will allow traffic on that port. - Comment: Add a comment for easy rule identification (e.g., "Allow RDP" or "Allow SSH").
- Additional optional specifications:
- Src. Address: You can specify specific IP addresses or ranges from which you want to allow access.
- Save the rule by clicking the Apply or Ok button.
- Chain: Set to
- Adjusting the rule order: For the rule to be reflected in the packet flow, move it above the last rule with the
dropaction.
Example of Blocking All Incoming Access to router services from Outside, Except for VPN Access:
The rule below must be ordered after any rule explicitly allowing traffic from VPN subnets. Also, set Available From for access services to IP addresses/subnets corresponding to the range of addresses assigned to VPN clients.
- Chain:
input - Src. Address: Allows specifying all addresses outside VPN subnets, or leave empty to block all external sources.
- Action:
drop


